I ran into an interesting problem these last couple days trying to work with a certificate and McAfee’s Web Gateway. Following the instructions to create a subordinate CA certificate and import into the Web Gateway console, I received an error:
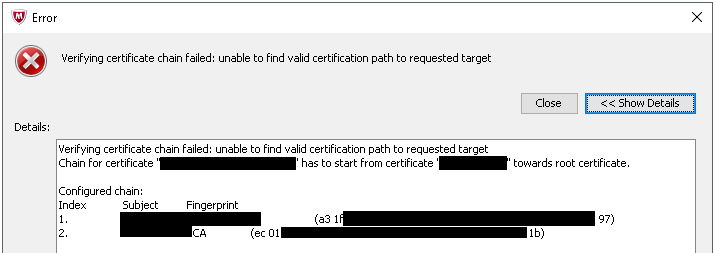
“Verifying certificate chain failed: unable to find valid certification path to requested target.
Chain for certificate “webgateway.domain.local” has to start from certificate “CAserver02.domain.local” towards root certificate.”
The End Goal:
McAfee’s Web Gateway is a filtering solution to ensure the security of the client organization while accessing resources on the internet. One option is to enable SSL Filtering, which is basically a man-in-the-middle attack, but on purpose. With SSL filtering enabled, the Web Gateway will inspect HTTPS traffic by unencrypting the packets, inspecting, and then re-encrypting with the client’s certificate. In this case, a Microsoft CA certificate.
You can choose to just use a self-signed cert from McAfee, but when clients reach a blocked page or a valid https site, they will get errors about the ssl certificate not being trusted – unless you deploy that self-signed cert to all the client PCs.
The better way is to deploy a certificate that the client PCs already trust. In this case, using a Microsoft Certificate Authority. For this particular client, an Offline Root CA [CAserver01] was deployed, and then a Subordinate domain joined CA [CAserver02] was added.
The process:
McAfee’s instructions here: https://kc.mcafee.com/corporate/index?page=content&id=KB75037
While it seems complicated, basically what happens is:
- Request a Subordinate certificate from the CA (in our case the Domain joined subordinate CA [CAserver02])
- Export that certificate with keys, and copy to the Web Gateway server
- Using openSSL commands, transform the cert into .pem files that WebGateway can understand
- SubCA-cert.pem
- SubCA-key.pem
- chain.pem
- Copy those files back to a Windows machine
- Using the Web Gateway web console, import the 3 files to complete
The import process is where I received the error.
The Solution:
After a while of troubleshooting, I figured out that the chain.pem file did not contain the proper chain.
I opened the chain.pem file in notepad at of course saw the typical:
—–BEGIN CERTIFICATE—–
(Lots of seemly random data here)
—–END CERTIFICATE—–
I inspected the chain.pem file by using the decoder utility on SSL Shopper and pasting the contents of the file. This showed me that the chain.pem file included the Offline Root CA [CAserver01], and not the Domain joined Subordinate CA [CAserver02].
So, I exported the Domain joined Subordinate CA’s cert [CAserver02] and converted it to the proper format. Again, opening in notepad, I verified the contents by copying and pasting it into the decoder utility. Once satisfied, I then replaced the contents of chain.pem.
Logging back into Web Gateway, and choosing the 3 files to import, the process was now successful.