AdminSDHolder is a container inside active directory that maintains a master list of permissions for objects that are members of privileged groups in active directory. Below are some of the groups:
- Administrators
- Domain Admins
- Enterprise Admins
- Schema Admins
- Domain Controllers
- Server Operators
- etc.
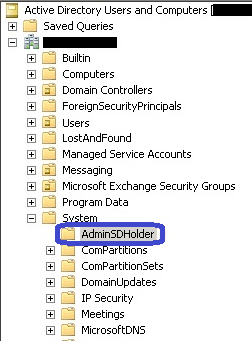
Basically, every hour, windows will compare the security permissions of an account (that is a member of a privileged group) to the permissions listed on the AdminSDHolder object, and if they are different, reset them. The AdminSDHolder object is in Active Directory under “System” (you will have to enable advanced features from the view menu in AD to view this folder).
This can become a problem is you don’t maintain a separate user account for administrative functions, and instead add your user account to the “domains admins” group. This will give you issues in the following two scenarios:
- Blackberry Enterprise Server (express also)
- Activesync with Exchange2010
Both of these will need to add a particular permission to the security of your user account object. (example - besadmin account will need “send as” permission for you account). If you are a member of a privileged group, that permission will disappear within the next hour, causing your blackberry to no longer be able to send messages. Likewise, you will be unable to use activesync on your Exchange2010 server.
Resolution- There are 2 ways to go about getting this to work. I highly recommend method 1 for best practices.
Method 1 -
 Maintain separate user accounts. One with no more permissions than a standard user. This is your daily account, used for logging into Windows, Exchange, and any other application. The second account is your administrative account, and can be added to “Domain Admins” and other privileged groups. You can use the “run as” feature of windows to use this elevated account when necessary. This will help keep you more secure, in case your account gets compromised.
Maintain separate user accounts. One with no more permissions than a standard user. This is your daily account, used for logging into Windows, Exchange, and any other application. The second account is your administrative account, and can be added to “Domain Admins” and other privileged groups. You can use the “run as” feature of windows to use this elevated account when necessary. This will help keep you more secure, in case your account gets compromised.
Method 2 -
 This method will add permissions to the AdminSDHolder object, making them part of the master list of permissions. (Example - adding the “send as” permission for the user BESadmin so that this will be automatically applied to any user account in a privileged group, just like the regular domain users have.)
This method will add permissions to the AdminSDHolder object, making them part of the master list of permissions. (Example - adding the “send as” permission for the user BESadmin so that this will be automatically applied to any user account in a privileged group, just like the regular domain users have.)
Open Active Directory Users and Computers, and from the View menu, choose “Advanced Features”. Now, under the System container, you will find AdminSDHolder. Right click and choose properties, and the security tab. From here, add the required permissions (like the BESadmin account with “send as” permission to user objects). Now, this will be added to all user objects within a privileged group.
In many places, the IT staff are members of Domain Admins, or the business owner is. Chances are, they will run into this issue.