With Windows Server 2008, there is the option to promote a member server to a RDOC, or Read Only Domain Controller. Just as the name suggests, it is a domain controller that is non-writable; read-only copy. The purpose of a RODC is actually simple: Security.
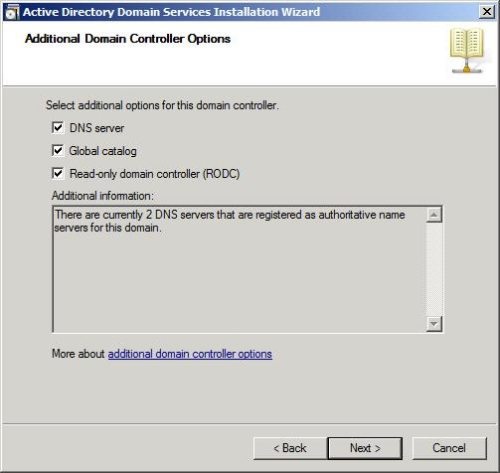 Instead of putting a regular DC at a small remote branch office, where the server sits in a closet with the cleaning supplies, consider making that DC read-only. In a perfect world, ever server would be behind locked doors, with restricted access - but that obviously is not so. By having a RODC onsite instead, the risk associated with that server being compromised is greatly reduced. This is due to the fact that a RODC doesn’t contain any user or computer credentials in it’s copy of Active Directory.
Instead of putting a regular DC at a small remote branch office, where the server sits in a closet with the cleaning supplies, consider making that DC read-only. In a perfect world, ever server would be behind locked doors, with restricted access - but that obviously is not so. By having a RODC onsite instead, the risk associated with that server being compromised is greatly reduced. This is due to the fact that a RODC doesn’t contain any user or computer credentials in it’s copy of Active Directory.
Actually, a RODC will only cache credentials for accounts that are specified. (This is specified in the Password Replication Policy for the RODC, and passwords are then stored in the non-writable copy of Active Directory) In this manner, only accounts of those at the branch office can be added to be cached. This will allow for fast user logins, instead of authenticating across a slow wan link to the main site’s domain controllers. If the read-only domain controller is compromised in any way, only those accounts would be at risk, and would need to be reset. In fact, if the RODC is compromised, when you deleted the RODC’s computer account in Active Directory, you will get the following prompts:
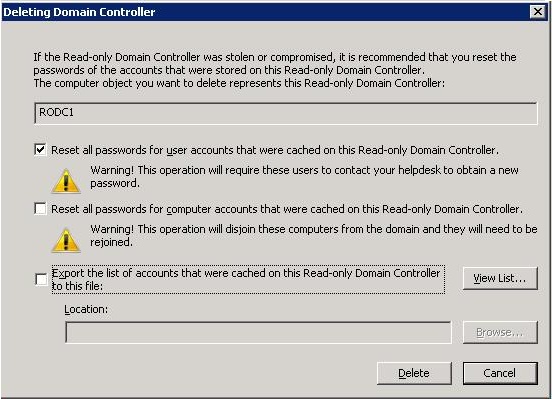 This will save administrators headaches and time. Instead of remembering what passwords were cached and then resetting each of them, it can be done automatically in one step. Please notice the warning for the second option: All computer’s accounts that were cached will no longer be joined to the domain.
This will save administrators headaches and time. Instead of remembering what passwords were cached and then resetting each of them, it can be done automatically in one step. Please notice the warning for the second option: All computer’s accounts that were cached will no longer be joined to the domain.
The only thing left would be to delete the RODC from Sites and Services also. Please note, this is not how to remove a regular DC. If a normal, writable domain controller is unavailable, and needs to be manually removed from the domain, NTDSutil needs to be used.
In order to be effective, an RODC should be in a separate site, and with accounts in that site specified to be cached. Any account with administrative privileges should NEVER be added to the caching (Password Replication Policy) list. A Read-Only Domain Controller isn’t for every situation, such as you have a fast enough WAN link, and a secure location to house the branch DC. However, for those interested in increasing domain security, it is worth implementing.